Contents
Configuring TLS for Oracle database connections (8.5.300.12+)
TLS configuration for UCS connecting to an Oracle database
Note that mutual TLS is not supported, only simple TLS.
Configuring UCS DAP in Configuration Server
The below procedure applies to both main and archive DAPs.
- Stop the UCS server.
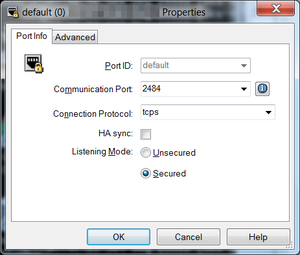
- Open the Oracle DAP used by UCS.
- Select the Server Info tab.
- Open the port to be secured.
- Type tcps in the Connection Protocol textbox.
- Select Listening Mode Secured.
- Click OK.
UCS Configuration
- Retrieve the required certificates.
- Ask the Oracle administrator to provide the Oracle certificate chain. This may include the root CA if your certificates are self-signed.
- Register the Oracle certificate(s) in the truststore file.
- Register on the UCS 8.5 server hosts (primary and backup) the chain of certificates that will be used to validate the Oracle server certificate with the Java truststore file. The following example uses keytool and a self-signed CA:
- keytool -import -trustcacerts -keystore /usr/lib/jvm/java-8-oracle/jre/lib/security/cacerts -storepass changeit -noprompt -alias "Genesys Internal CA" -file ~/ca-intermediate.crt
- Configure UCS to use your truststore file.
- Truststore can be configured by specifying Java environment variables in contactServer.sh or ContactServerDriver.ini.
- -Djavax.net.ssl.trustStore=/usr/lib/jvm/java-8-oracle/jre/lib/security/cacerts
- -Djavax.net.ssl.trustStoreType=jks
- -Djavax.net.ssl.trustStorePassword=changeit
- You may also need to specify common cipher suites to use. Please refer to Java SSL vendor documentation for more details.
- Start UCS 8.5 server.
This page was last edited on October 31, 2018, at 19:30.
Comments or questions about this documentation? Contact us for support!