Testing with ZAP Proxy
The ZAP Proxy is a development tool that allows you to test your application without adding the JavaScript tracking code to your website. Once you have configured this proxy, you can launch it and start the Genesys Web Engagement servers to start testing your application by emulating a visit on your website. In a few clicks, without modifying your website, Genesys Web Engagement features will show up on a set of web pages, according to the rules and categories that you created.
There are two proxy tools available in the Genesys Web Engagement installation: Simple and Advanced. See the appropriate tabs below for details and configuration information.
To use the Simple ZAP Proxy, you must first complete a few procedures to configure the tool and your web browser.
Getting the ZAP Proxy Port
Complete this procedure to retrieve the ZAP Proxy port, which you will need later when you configure your web browser.
Start
- Navigate to C:\Users\current user\ZAPProxy.
- If this folder does not exist, navigate to your Web Engagement installation directory and launch proxy.bat (on Windows) or proxy.sh (on Linux). The ZAPProxy folder appears automatically.
- Edit config.xml and find the <proxy> tag.
- Check that the value of the <ip> tag is set to your host IP address.
- Note: You cannot use 127.0.0.1 or localhost for this value.
- Note the value of the <port> tag (usually 15001).
- Save your changes.
End
Configuring the Proxy
Start
- Navigate to the \tools\proxy\plugin folder inside your your Web Engagement installation directory.
- Open the configuration file, which is called FilterMultiReplaceResponseBody.xml.
- Change <enable>false</enable> to <enable>true</enable>.
End
Starting the Proxy
Navigate to your Web Engagement installation directory and launch proxy.bat (on Windows) or proxy.sh (on Linux). The Simple ZAP Proxy starts.
Setting Up your Web Browser
Configure your web browser to use the Simple ZAP Proxy.
Start
- Start your web browser.
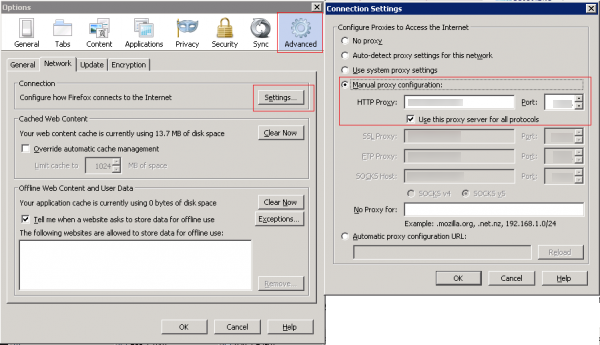
- Open your Internet settings. For instance, in Mozilla Firefox, select Tools > Options. The Options dialog window appears.
- Select Advanced, and in the Network tab click Settings... The Connection Settings dialog windows appears.
- Select the Manual proxy configuration option:
- Enter your host IP address in the HTTP proxy text box.
- Enter the port used by the ZAPProxy in the Port text box. This is the value you retrieved in Getting the ZAPProxy Port.
- Select the option Use this proxy server for all protocols.
- Click OK. Now your browser is set up for the ZAP Simple Proxy. To use the proxy, all you need to do is navigate to the site where you want the proxy to inject the Web Engagement instrumentation script and browse through the web pages.
End
The Advanced ZAP Proxy is based on the
OWASP Zed Attack Proxy Project (ZAProxy). In addition to acting as a proxy, the Advanced ZAP Proxy also provides a UI and validates vulnerabilities in your website at the same time.
To use the Advanced ZAP Proxy, you must first complete a few procedures to configure the tool.
Starting the Proxy
Navigate to your Web Engagement installation directory and launch tools\proxy\zap.bat (on Windows) or tools\proxy\zap.sh (on Linux). The proxy starts.
Configuring the Proxy
Once the proxy is running, you can configure it using the GUI.
Start
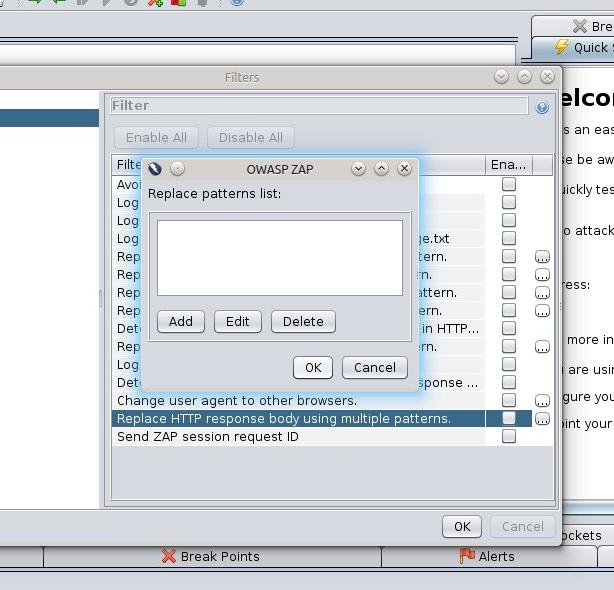
- Open Tools > Filter....
- In the list of filters, select Replace HTTP response body using multiple patterns and click ... to edit the filter.
- Click Add and enter the following information:
- Pattern - </head>
- Replace with -
<script> var _gt = _gt || []; _gt.push(['config', { dslResource: ( 'https:' == document.location.protocol ? 'https://<Web Engagement Server host>:<Web Engagement Server port>' : '<Web Engagement Server host>:<Web Engagement Server port>') + '/server/resources/dsl/domain-model.xml', httpEndpoint: '<Web Engagement Server host>:<Web Engagement Server port>', httpsEndpoint: '<Web Engagement Server host>:<Web Engagement Server secure port>' }]); var _gwc = { widgetUrl: ( 'https:' == document.location.protocol ? 'https://<Web Engagement Server host>:<Web Engagement Server port> : '<Web Engagement Server host>:<Web Engagement Server port>') + '/server/resources/chatWidget.html' }; (function(gpe, gwc) { if (document.getElementById(gpe)) return; var s = document.createElement('script'); s.id = gpe; s.src = ( 'https:' == document.location.protocol ? 'https://<Web Engagement Server host>:<Web Engagement Server port>' : '<Web Engagement Server host>:<Web Engagement Server port>') + '/server/resources/js/build/GPE.min.js'; s.setAttribute('data-gpe-var', gpe); s.setAttribute('data-gwc-var', gwc); (document.getElementsByTagName('head')[0] || document.body).appendChild(s); })('_gt', '_gwc'); </script> </head> - Click OK to save the pattern.
- If you need to check or update the ZAP port address, open Tools > Options... and review the Local proxy section.
End
Configuring the URL Filter
Complete this procedure to use the GUI to configure URLs that the proxy should ignore.
Start
You can exclude a site in one of two ways:
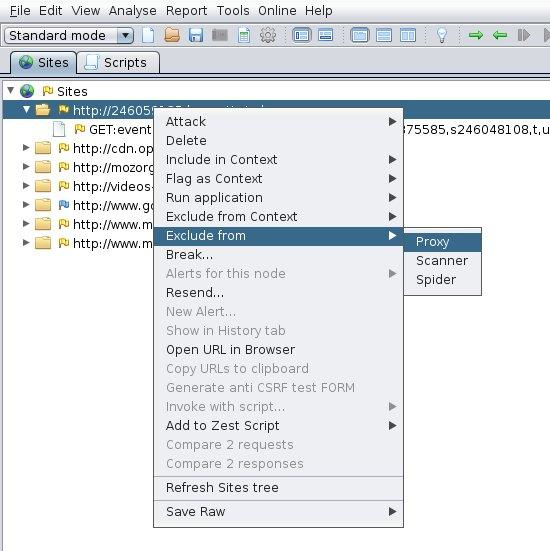
- In the Sites tab, right-click on a site and select Exclude from > Proxy.
- Select File > Properties. In the Session Properties window, select Exclude from proxy, add your URL, and click OK.
- If you want the proxy to remember the excluded URLs beyond the current session, select File > Persist session... and select a file to save your session.
End
Working with the Proxy
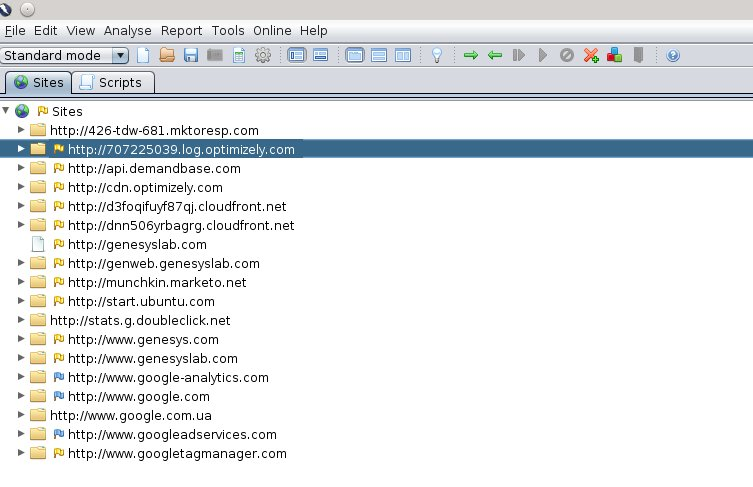
After you have configured the proxy, keep it open and open up a web browser. Now you can browse through your web pages that are instrumented with Genesys Web Engagement and they will be displayed in the Sites tab of the proxy GUI:
For more information about working with ZAProxy, see https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project.
Genesys performs security testing with
OWASP Zed Attack Proxy (ZAProxy) to make sure the Genesys Web Engagement solution is invincible to known attacks.
ZAP Overview
The ZAProxy is an easy-to-use, integrated penetration testing tool for finding vulnerabilities in websites and web applications.
Among others, ZAProxy supports the follow methods for penetration security testing:
Genesys uses both methods.
Passive Scan Overview
ZAP is an Intercepting Proxy. It allows you to see all of the requests made to a website/web app and all of the responses received from it. For example, you can see AJAX calls that might not otherwise be obvious.
Once set up, ZAP automatically passively scans all of the requests to and responses from the web application being tested.
While mandatory use cases for the application that is being tested are followed (either manually or automatically), ZAProxy analyzes the requests to verify the usual operations are safe.
Active Scan Overview
Active scanning attempts to find potential vulnerabilities by using known web attacks against the selected targets. Active scanning is an attack on those targets. ZAProxy emulates known attacks when active mode is used.
Through active scanning, Genesys Web Engagement is verified against the following types of attacks:
- Spider attack — Automatically discovers all URL links found on a web resource, sends requests, and analyzes results (including src attributes, comments, low-level information disclosure, and so on).
- Brute browsing (based on the Brute Force technique) — Systematically makes requests to find secure resources based on known (commonly used) rules. For example, backup, configuration files, temporary directories, and so on.
- Active scan — Attempts to perform a predefined set of attacks on all resources available for the web resource. You can find the default set of rules here.
- Ajax spider — Automatically discovers web resources based on presumed rules of AJAX control (JS scripts investigation, page events, common rules, dynamic DOM, and so on).
References
If you want to examine your website against vulnerabilities in a similar way, refer to the OWASP Zed Attack Proxy Project or other documentation to learn about how to perform security testing with ZAP.