Contents
Specific connection configuration details
iWD follows the common Genesys approach and recommends using Host-level configuration with PEM-files on Linux and Windows certificates on Windows for all PSDK connections, REST clients and JMS client. For REST servers, Connection-level configuration with JKS-files is recommended. For JDBC clients the recommended way is to use JKS files and configure connection via JVM options.
Assumptions/Prerequisites
- You have generated certificates with associated private and public keys.
- You have Java keystore and truststore files with the same keys.
Please find more information about certificates here.
ActiveMQ
To configure SSL in ActiveMQ, please refer to the vendor's ActiveMQ documentation.
Sample ActiveMQ SSL configuration
The following is an example of how you might configure SSL for ActiveMQ.
- Copy keystore.jks and truststore.jks into the <Apache ActiveMQ installation directory>/conf folder.
- Open the <Apache ActiveMQ installation directory>/conf/activemq.xml file and add the following lines:
<transportConnectors> ... <transportConnector name="ssl" uri="ssl://0.0.0.0:61617?trace=true&needClientAuth=true"/> ... </transportConnectors> <sslContext> <sslContext keyStore="file:${activemq.base}/conf/keystore.jks" keyStorePassword="YourKeyStorePassword" trustStore="file:${activemq.base}/conf/truststore.jks" trustStorePassword="YourTrustStorePassword" /> </sslContext> - Change keystore and truststore passwords accordingly.
- Restart ActiveMQ.
JDBC configuration
Please read the Configuring database connections topic.
Windows certificates import
For the Windows certificates installation procedure please see the Windows certificates topic.
Framework configuration
Configuration Server
Configure the auto-upgrade port as described in Securing core framework connections topic.
Interaction Server, UCS, Message Server
Configure secured ports as described here.
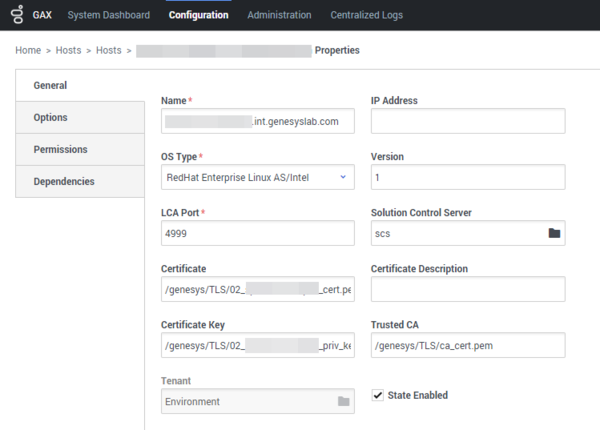
Host configuration
- Open GAX -> Hosts -> <your_host> -> and fill the certificate fields with your PEM certificate files.
- Open the Options tab and add the following options:
- [security]/tls = true
- [security]/mutual-tls = true

Troubleshooting
If you start receiving ESP Server is not connected interaction errors and tasks, do the following:
- Go to the ErrorHeld queue, add the tls=1 transport parameter to the connection between Interaction Server and GRE or the GRE cluster application and GRE nodes.
- Add the tls=1 transport parameter to the connection between Interaction Server and Universal Contact Server.